OIDC Authentication
For self-hosted deployments, LlamaCloud supports authenticating users via OIDC. This will enable you to use your own identity provider (IdP) to authenticate users. We support most of the OIDC protocol, but there are some gaps. If you have questions or would like to request a new feature, please don't hesitate to reach out.
note
OIDC is the only supported authentication mode at the moment. More options are coming soon!
Requirements
- Your IdP supports using a discovery URL or issuer URL.
- The required scopes are
openid,profile, andemail.
In your values.yaml file, you can configure the following:
backend:
config:
oidc:
clientId: "your-client-id"
clientSecret: "your-client-secret"
discoveryUrl: "your-discovery-url"
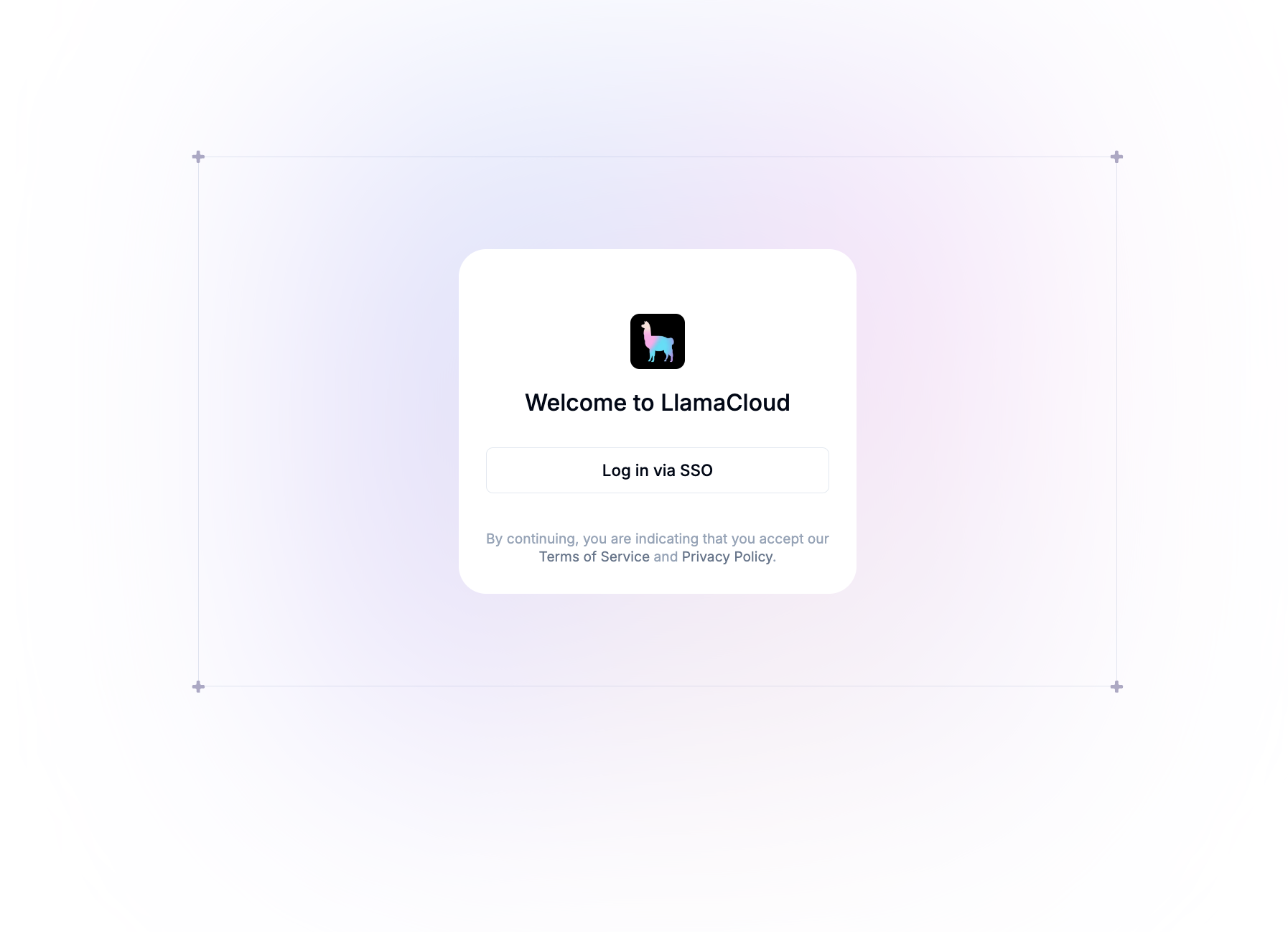
After you've configured the above, you should see the following in the UI:
Possible Gotchas
- A valid OIDC discovery URL must end in
.well-known/openid-configuration. - In test environments, you may need to disable SSL verification if your OIDC provider does not have a valid SSL certificate. This is not recommended for production environments. To bypass SSL verification, you can add the following to your
values.yamlfile:-
backend:
extraEnvVariables:
- name: OIDC_VERIFY_SSL
value: false
-